3 attacks vectors
Satellite attacks fundamentally differ from traditional pentests by their unique attack surface, organized around three critical entry points :
1. Ground Segment
Ground stations represent the most vulnerable link in the chain. These infrastructures include control centers, communication antennas, and mission management systems. Unlike satellites in orbit, these systems are directly accessible via the Internet and suffer from the same vulnerabilities as classical IT infrastructures, such as phishing, exploitation of CVEs, unauthorized access, etc...
2. Space Segment
Satellites present unique challenges for pentesting. They operate with often outdated embedded systems, without the possibility of quick updates, and in a hostile environment (radiation, thermal constraints). The communication protocols used (CCSDS, proprietary) are often poorly documented and insecure.
3. Supply Chain
This is an often overlooked aspect; the satellite supply chain involves many subcontractors and integrators. Malicious COTS (Commercial Off-The-Shelf) components can compromise an entire satellite via the "SpyChain" attack.
To get a better understanding and classify the threats facing space systems, the SPARTA (Space Attack Research and Tactic Analysis) matrix developed by The Aerospace Corporation catalogs all the tactics, techniques, and procedures (TTP) used by attackers in the space domain. Comparable to the MITRE ATT&CK framework but specifically dedicated to space missions. The SPARTA matrix constitutes an unclassified knowledge base detailing adversary behavior and possible actions throughout the lifecycle of an attack against a satellite or space system.
The most common attacks
Most common attacks are as following:
1. Eavesdropping
Eavesdropping on satellites means that it is possible to listen to or remotely intercept communications that travel between a satellite and a ground station. These communications use radio waves across a range of frequencies, between 30 MHz and 60 GHz.
Malicious individuals can use devices such as software-defined radios (SDRs) or other specialized hardware to capture these radio signals. Once intercepted, they can retrieve exchanged data such as messages, calls, or Internet information, especially if those communications are not well protected or encrypted.
2. Jamming
This attack aims to disrupt or interrupt a satellite's radio frequency communications by overwhelming the channels with interfering signals.
Imagine a conversation on Teams or another platform where someone shouts so loudly that they drown out everyone else's voice. This makes communication impossible. Similarly, satellite jamming sends strong interfering signals that saturate the channels, preventing the satellite from communicating normally.
3. Spoofing
This type of attack consists of generating and transmitting fake signals that imitate legitimate satellite signals (often GPS or GNSS), with the goal of deceiving a targeted receiver. It is a sophisticated positioning spoofing technique that creates falsified signals to mislead receivers, which can have major consequences for the security of both space-based and ground systems that rely on satellite positioning.

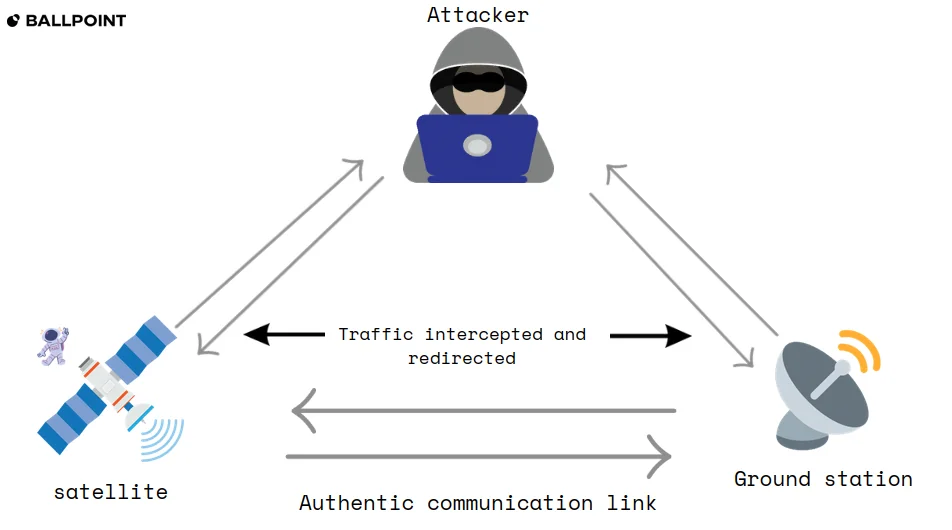
4. Man-in-the-Middle (MitM)
Man-in-the-Middle attacks involve intercepting and potentially altering communications exchanged between two legitimate for example, between a ground station and a satellite or an end user. This interception process allows the attacker to spy on data, inject malicious content, or manipulate the commands being transmitted.
This section presents some of the most common attacks targeting space systems, but it represents only a limited overview compared to the growing diversity and complexity of cyber threats facing satellites and their associated infrastructures. Among the different types of possible attacks, the ground segment remains the weakest and most vulnerable link.
Example case : Viasat
The 2022 attack targeting Viasat's KA-SAT perfectly illustrates this vulnerability. The attackers compromised a ground station in Turin, Italy, by exploiting a vulnerability in a Fortinet device, and then used the satellite infrastructure as a propagation vector to deploy the "AcidRain" malware to thousands of customer modems.
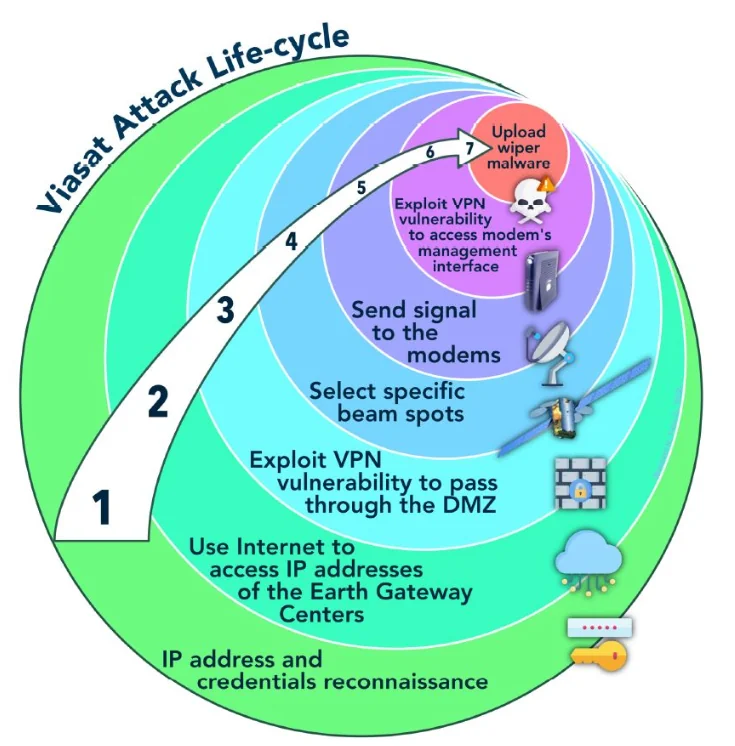
- Phase 1: Reconnaissance of IP addresses and credentials
- Phase 2: Access to ground gateways
- Phase 3: VPN exploitation
- Phase 4: Beam selection
- Phase 5: Transmission of malicious signals
- Phase 6: Access to management interfaces
- Phase 7: Deployment of the AcidRain wiper
The reconnaissance phase in the Viasat KA-SAT attack was the primary factor that allowed the attackers to gain initial access. During the DEF CON 31 presented by Mark Colaluca and Nick Saunders (Viasat experts who investigated the incident), it was revealed that the attack exploited two distinct sets of compromised credentials originating from either:
- The 2021 Fortinet leak: 500,000 VPN credentials were disclosed, 7.96% of which were associated with Italy.
- And/or exploitation of CVE-2018-13379: a FortiOS vulnerability enabling the extraction of credentials directly from unpatched systems.
The credentials have been used to:
- First set : Fortinet VPN credentials used for initial access.
- Second set : Credentials used to pivot toward the management servers.
The attackers' initial access occurred through the Internet by exploiting a vulnerability in the Fortinet VPNs securing the entire Skylogic/KA-SAT ecosystem from the central management servers to the terrestrial transmission stations (gateways) and even residential modems. Ruben Santamarta confirmed that this vulnerability in Fortinet appliances served as the pivotal entry point, enabling the compromise of the entire command-and-control chain.
Viasat reported that the attackers gained access to the infrastructure via the Internet by specifically targeting Fortinet VPN equipment securing all critical elements of the chain: Skylogic's administrative servers, the terrestrial gateways connecting the satellites to the Internet, and the SurfBeam2 client modems providing connectivity to end users.
Post-incident forensic investigations revealed that the attackers exploited a configuration error in the Fortinet VPN equipment to bypass perimeter protections and gain direct access to the internal management network segment (trusted management segment) of the KA-SAT system, which is normally protected and isolated from the Internet.
Although Fortinet had released a security patch to address this vulnerability, there is no evidence confirming that Skylogic applied it to its infrastructure. This presumed negligence may have allowed the attackers to exploit the vulnerable and unpatched VPN to penetrate, from the public Internet, the terrestrial stations (Gateway Earth Stations) or the Points of Presence (POP) servers managed by Skylogic.
The attackers then moved laterally through this trusted management network toward a specific network segment used to manage and operate the modem network.
This access allowed the attackers to bypass the DMZ and reach the satellite intranet network operating in bent-pipe mode, that is, merely relaying data without local processing, a function normally restricted to authorized administrators. This architecture enabled the attackers to penetrate all the way to the end-user SurfBeam2 modems.
The attack did not impact all Viasat modems across the KA-SAT network but only a specific geographical selection. This selectivity was made possible by the satellite's multi-beam architecture. From the terrestrial stations (Gateway Earth Stations), operators can individually enable or disable each of the 82 geographic cells (spot beams) covering Europe and the Mediterranean basin. The attackers therefore deliberately chose the geographic areas where modems would be infected through commands containing the AcidRain wiper.
The attackers moved laterally through this trusted management network toward a specific network segment used to manage and operate the system, then leveraged this network access to execute legitimate and targeted management commands on a large number of residential modems simultaneously.\nMore specifically, these destructive commands overwrote key data in the modems' flash memory, rendering them unable to access the network but not permanently unusable.
The attackers hijacked the legitimate update distribution infrastructure of the KA-SAT network, turning the official management system into a vector for a supply chain attack. This compromise enabled the large-scale deployment of a destructive malware specifically developed to target the MIPS architecture of satellite modems and routers.
The Viasat attack therefore stands as a textbook example of a ground segment attack that simply leveraged the satellite as a legitimate distribution infrastructure to maximize the geographical impact and scalability of the destructive operation.
Ressources to look at