My name is Loup, and I am a work-study pentester at Ballpoint, studying for a master's degree in cybersecurity at ESGI since the beginning of September. Before joining Ballpoint, I wanted to develop my skills independently, using the Hack the Box and HTB Academy platforms. So I signed up for the certification that would allow me to progress the most, which is starting to be well recognized in technical circles, and would fit my student budget: the CPTS. I wanted to give feedback from the perspective of a relatively novice student, as most of the existing online feedbacks comes from experienced pentesters.
The CPTS (Certificate Penetration Tester Specialist) is offered by Hack The Box Academy, a platform of the Hack The Box group, known for its CTF content and training at all levels since multiple years. The content covers a wide variety of technical topics:
- Introduction to pentesting (methodology, concept, vocabulary)
- Reconnaissance
- Web application exploitation
- Linux & Windows host attacks
- Linux & Windows privilege escalation
- Manual and automated exploitation
- Pivot and lateral movement between different internal networks
- Active Directory enumeration, abuse, and exploitation
- Post-exploitation and looting
- Documentation and report writing
- Differences between types of audits
Although some of these terms may seem complex to beginners like me when starting out, the format offered by Hack The Box guarantees a “smooth” learning experience, with regular practical exercises to ensure understanding of the course.
In order to take the exam, candidates must complete the modules that are part of the “Job Path Penetration Tester” available on the platform. The courses currently consist of 28 modules of varying sizes, divided by theme, with some modules dedicated to a specific type of attack, such as the web module “Local File Inclusion,” which is exclusively in English and has no audio support available.
The modules are divided into pages, each covering a notion/concept related to the theme. Most pages end with questions to be completed, which are necessary for the completion of the modules. Generally, these questions concern an instance, hosted by Hack The Box, which is vulnerable and allows the concepts covered to be applied manually, using the solutions (commands) available in the course.
In addition, most modules conclude with one to three “skill assessments,” vulnerable instances designed to apply the atacks explained in the module, this time without the solutions, in order to check understanding of the subject and avoid a loop of Ctrl+C/Ctrl+V.
Personal background
In terms of education, I have a bachelor's degree in System and Network Administration, which I completed through a work-study program, providing me the networking and system basics required for the modules (HTB Academy does, however, offer another set of modules to provide these basics to beginners).
Before starting the CPTS, I had mainly learned about offensive security using the main Hack the Box platform, completing the easy, medium, and hard boxes that are released weekly.
It is not mandatory to complete them entirely on your own, especially the first ones, where you have to learn how to search in addition to the challenge of the box itself. I also participated in a few team CTFs and regularly attended the HTB France community meetups, held every two weeks, which include guides to previous boxes, demos of cybersecurity tools, and feedback sessions.
As I was taking a gap year, I was able to devote a significant amount of time to the modules, around 8 hours a day, 5-6 days a week, completing the entire course in 3.5 months. I don't particularly recommend this fairly intense pace, which can lead to skimming over certain “details” after 6-7 hours, wasting time during the exam to find the information. As for many, the “Active Directory enumeration and attack” module was the most complex for me, due to the amount of information included and the Windows & Powershell prerequisites that had to be mastered for this module.
Additional preparation
 In addition to the required modules, I added the “Using crackmapexec” module to my list (the maintained version is netexec, but the module commands remain valid just by replacing the tool name, with many additional options). This is a tool that allows you to execute a wide range of attacks related to Active Directory (and more) from Linux. It is based on Impacket scripts, but also provides its own features.
In addition to the required modules, I added the “Using crackmapexec” module to my list (the maintained version is netexec, but the module commands remain valid just by replacing the tool name, with many additional options). This is a tool that allows you to execute a wide range of attacks related to Active Directory (and more) from Linux. It is based on Impacket scripts, but also provides its own features.
Completing certain pro-labs offered by HTB is also an advantage. Dante and Zephyr allowed me to practice working in complex environments, through several pivots, and encounter a number of limitations related to network constraints and overcome them. Dante is a web/local escalation-oriented lab, while Zephyr is more AD-oriented, allowing us to target the skills we want to develop. Although some attacks in these environments are not explained in the courses, this also challenges our ability to search for information online when faced with unknown technologies/attack vectors.
More than pure knowledge, methodology and a “think outside the box” mentality are key to success in these prolabs. They allowed me to gain confidence and not get stuck several times during the exam.
The exam
The exam format is 10 days, unsupervised and with no restrictions on resources/tools (except for outside human assistance, which is prohibited). When you purchase a voucher, two attempts are included. Once the first attempt is completed, HTB provides feedback within a maximum of 21 business days. The waiting time is not related to the result; feedback is provided in “batches” at regular intervals.
In the event of failure, the HTB examiner provides feedback on the report and a list of tips/modules to review before retaking the exam, which must be started within 10 days of receiving the result.
However, don't expect any clues if you get stuck; the advice is generic in order to improve your methodology/mindset for your second attempt. Without going into detail, two pieces of advice that come up regularly in the modules become crucial during the exam: “enumerate everything” and “be flexible on your tooling.” You may find yourself “unraveling the thread” of the exploit, piecing together information, and hitting a wall because a tool is not returning the correct output. When several elements fit together, it is always a good idea to try a second method/tool before giving up on that lead ;)
In addition to finding a minimum number of flags during the exam, you must also provide a commercial-quality report within the same time frame. The penultimate module of the course is dedicated to this report and is very comprehensive in terms of expectations.
In addition, the Sysreptor tool includes a template for this exam, making it much easier to write. Among other things, the report must contain an “executive summary,” designed to be read by a non-technical audience, in order to provide an overview of the problems and areas for improvement, a step-by-step guide for each domain compromise, so that it can be reproduced by a company technician, and a section detailing each vulnerability found, its impact, and how to remedy it. Even if you don't manage to achieve the number of flags required to pass the exam, I advise you to write a report on what you found. This reduces the risk of failing the second time because your report does not meet the expected standards.
In terms of difficulty, the machines are generally medium, with one or two hard ones in my experience. Anyone who can complete medium boxes on the main platform in a few hours and takes good notes during the course should be able to pass the exam. It's normal to get stuck; I myself lost more than four days on certain flags, which meant I ran out of time on my first attempt. Failing the first attempt is nothing to be ashamed of; HTB includes a second attempt for good reason. It's easy to fall into “rabbit holes,” false leads left more or less intentionally to mimic a real-world environment, where not everything that can be exploited in theory always leads to an escalation of privileges. The lab can also be unstable at times, so restarting a command twice or resetting the instance when there is a suspected vulnerability can be a lifesaver.
Note-taking
Personally, I used Obsidian for note-taking. If you tend to take screenshots often, I recommend CherryTree, which allows you to organize them better. I used a simple organization: 1 file = 1 module (be careful with certain modules such as “Active directory enumeration and attacks” which could slow down when opening if not separated into several files), as well as a separate file for solutions to exercices, skill assessments and “tips” discovered during skill assessments to fix certain bugs or write down malfunctions of certain tools/versions.
Tips
Modules
- Don't neglect anything when taking notes: everything mentioned in the modules may be useful, either in the exam or later in pentesting.
- Remember to include links to additional resources: you can create a CPTS folder in your favorites to collect them.
- When the module offers several methods to test, try as many as possible. This will help you become more flexible with the tooling.
- Set yourself goals: e.g., a minimum of 6 hours per week, 3 modules per month, etc.
- Don't hesitate to ask for help: Discord and Reddit are there if an explanation isn't clear to you. There's no shame in it, everyone stumbles before they learn to walk.
- Use your own VM with exegol: during the exam, the pwnbox provided by HTB does not last for the entire 10 days of the exam, making it a risky choice since yoou will need to reuse elements in the report. In my opinion, the best option is to host an Ubuntu VM on your own PC with Virtualbox and installing Exegol, a dedicated container wrapper for pentesting, whose installation guide is available here.Using this solution during class allows you to get used to the environment and be ready for the exam.
Exam
- List all the targets you can find before, during, and after compromising a machine (in accordance with the letter of commitment provided at the beginning of the exam).
- Use sysreptor self-hosted for the report: Some parts are already completed, with the expected wording and sections already in place. I preferred the self-hosted version to avoid maintenance and to be able to work on it offline. With exegol on a docker VM already installed, the remaining installation is minimal.
- Avoid tunnel vision: If you are stuck at a stage for more than a few hours, check the other available targets/vectors.
- Vary the tools: If a trail of several elements comes to a dead end, try another approach to get the result. Some tools are poorly maintained, may be prone to bugs, or may have incomplete documentation.
- Prefer code blocks (three ` in markdown syntax, used by sysreptor) to screenshots outside of web applications and rdp sessions, as this will greatly reduce the size of the final file (less than 2 MB for mine).
- Take notes on everything, even tests that didn't work, to avoid repeating the same test three or four times. This also ensures that you have everything you need for the report, avoiding having to redo half the lab for a command when writing the report.
Price
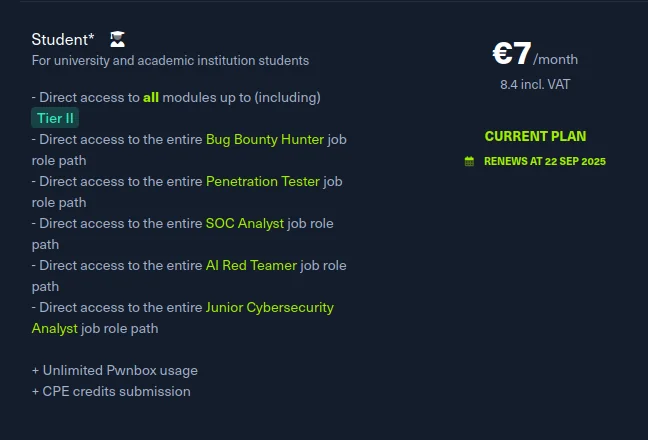
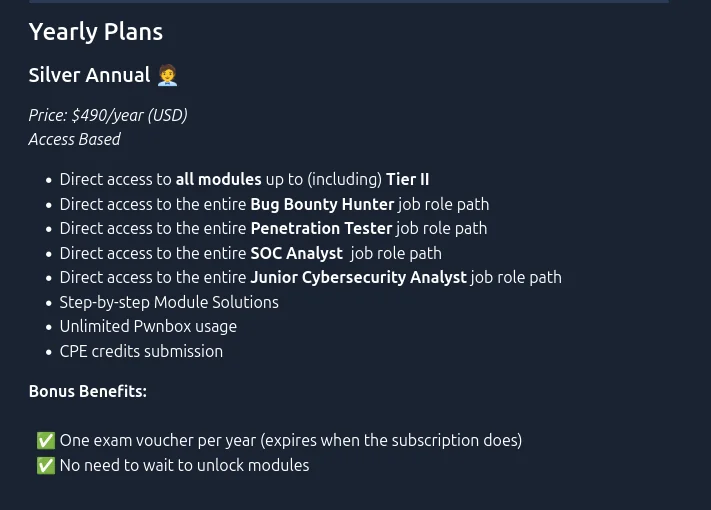
Thanks to my school email address, I was able to have access to all the required modules for €8.40 per month, including taxes. The voucher (ticket to access the exam, which includes two attempts) costs €216 including taxes, which means a budget of around €250 including taxes for a student at my pace, or ~€275 at a slower pace. Although this is still a significant amount for a student, this certification is much more accessible than its main competitor, the OSCP (from $1,599 to $2,000), which, according to the feedback I have received, is inferior from a technical point of view and more CTF-like in nature.

If you are not a student, the most interesting option in my opinion is the silver annual subscription, which gives you access to 4 “job paths” and their exams at no extra cost for ~$592 including taxes. Although this doubles the amount invested, it is still the most attractive option compared to purchasing “cubes” directly, the internal currency of HTB, which costs €488 for only the CPTS modules with the voucher. Here, it is possible to take courses for four certifications and receive one voucher for the CJCA (beginner level certification) and one voucher to choose from among the three other certifications.