In an increasingly digitalized world, cybersecurity has become a priority for businesses of all sizes. Yet, despite technological advancements and sophisticated protection solutions, one threat remains ever-present: social engineering. Unlike purely technical attacks that exploit software vulnerabilities, social engineering targets human psychology to bypass security systems.
SMEs, even though they are investing more and more in cybersecurity solutions, remain particularly vulnerable to these attacks. Why? Because the most exploitable weakness in any IT system is still the human factor.
What is social engineering ?
Social engineering is a psychological manipulation technique used by cybercriminals to deceive employees into disclosing sensitive information, carrying out malicious actions, or granting access to secured systems. These attacks exploit various human factors, such as trust, urgency, fear, or a false sense of authority.
Cybercriminals rely on a fundamental principle: it is often easier to trick a person than to bypass an advanced cybersecurity system.
Concrete examples of social engineering
1. Phishing
The most common attack involves sending fraudulent emails that mimic legitimate companies (banks, suppliers, government agencies, etc.). A single click on a malicious link can allow hackers to steal confidential information (login credentials, passwords, banking details).
💡Example: Between 2013 and 2015, a Lithuanian scammer managed to steal over $100 million from Google and Facebook by sending fake invoices that appeared to come from an Asian supplier. The two tech giants unknowingly processed the payments.
🔗 Learn more about phishing attacks
2. Vishing
Cyber-criminals use phone calls to obtain sensitive information by impersonating a colleague, partner, or IT provider.
💡 Example: In 2020, attackers pretended to be bank representatives, calling victims to inform them of "suspicious activity" on their accounts. Under the pretense of securing the accounts, they successfully obtained personal and banking information.
🔗 Learn more about vishing
3. Baiting
Attackers intentionally leave infected USB drives in strategic locations (parking lots, meeting rooms, open spaces), hoping that a curious employee will insert one into their computer.
💡 Example: In 2016, a study showed that 48% of people who found a USB drive plugged it into their computers, potentially executing malware.
🔗 Learn more about baiting
4. Spear Phishing
A cyberattack in which attackers send fraudulent emails specifically designed for a person or organization. Unlike classic phishing, which targets a broad audience, spear phishing relies on extensive research on the victim to make the attack more credible and effective.
💡Example: In 2018, the French company Pathé fell victim to a spear phishing attack. Cybercriminals impersonated senior executives and sent emails to financial managers, urging them to transfer €19.2 million to fraudulent accounts. The emails looked authentic, using addresses similar to those of company leaders and appropriate language, successfully deceiving employees.
🔗 Learn more about spear phishing
Attack cycle of social engineering
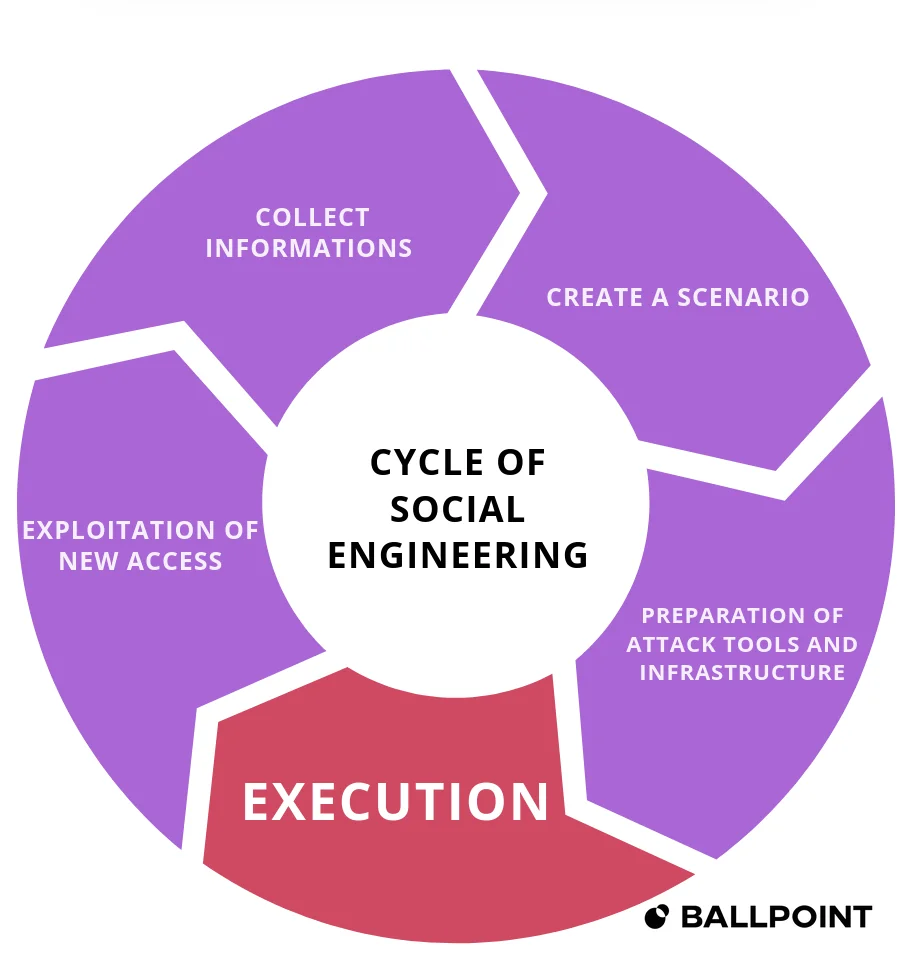
Why are SMEs prime targets ?
Unlike large corporations that have dedicated cybersecurity teams and regular employee training, SMEs are often less prepared and more vulnerable. Here’s why :
- Lack of Awareness – Many employees are unaware of the manipulation techniques used by cybercriminals.
- Limited Resources – SMEs often lack the budget to invest in advanced cybersecurity solutions.
- Weak Security Protocols – Payment and access validation procedures are often more flexible, making attacks easier.
- Minimal IT Supervision – SMEs rarely have a dedicated IT department, leading to insufficient access monitoring.
- False Sense of Security – Many business owners believe their company is "too small" to attract hackers. In reality, SMEs are often easier targets and can serve as entry points to larger partners.
How to protect against social engineering ?
Fortunately, there are several best practices to reduce the risk:
Train and Educate Employees
The best defense is awareness. Organizing regular training sessions and attack simulations (e.g., fake phishing emails) helps reinforce security reflexes.
Verify Suspicious Requests
- Never share sensitive information without prior verification.
- If you receive an urgent request via email or phone, contact the person directly through another channel.
Establish Strict Validation Procedures
- Require dual validation for any financial transaction.
- Verify bank account changes by directly contacting the supplier.
Restrict Access to Sensitive Information
- Employees should only have access to resources necessary for their job.
- Implement multi-factor authentication (MFA) to secure logins (soon to be mandatory on Microsoft Entra)
Use Appropriate Cybersecurity Tools
- Install anti-phishing solutions for emails
- Enable alerts for suspicious login attempts.
- Use VPNs and secure connections for remote work.
Conclusion
Social engineering exploits a vulnerability that antivirus software cannot detect: the human factor. It does not rely on technical weaknesses but rather on psychological manipulation and a lack of cybersecurity awareness.
For small and medium-sized businesses, the challenge is significant: securing infrastructure alone is not enough. It is equally crucial to train and educate employees. By fostering a culture of vigilance and security, businesses can significantly reduce risks and avoid falling victim to cybercriminals.